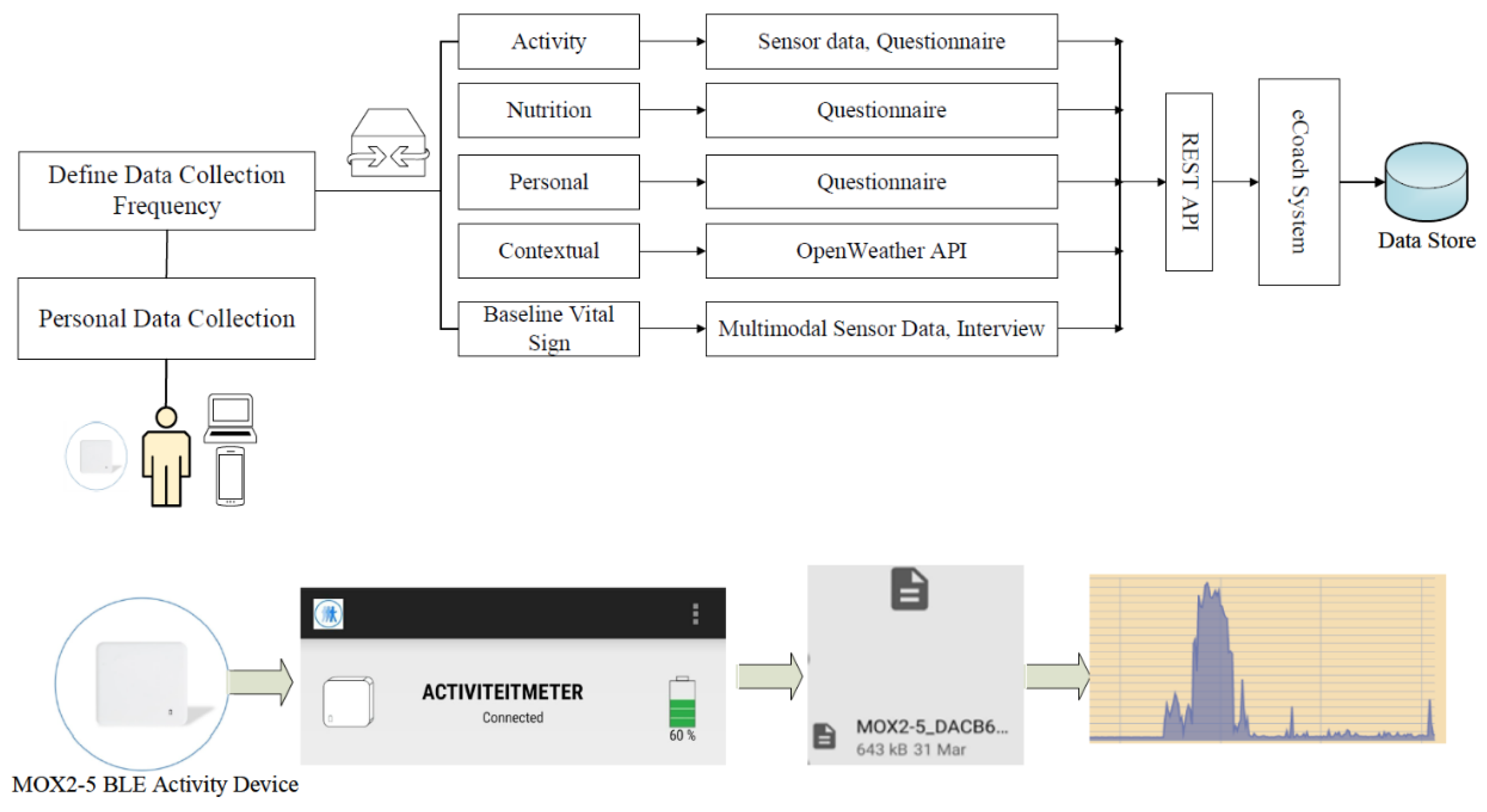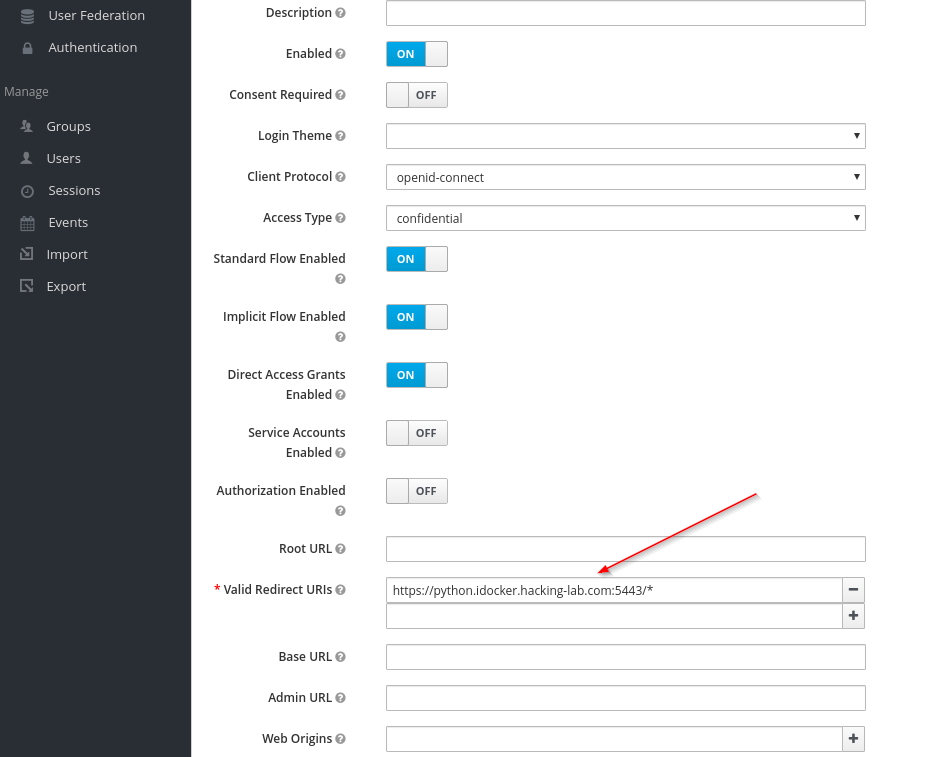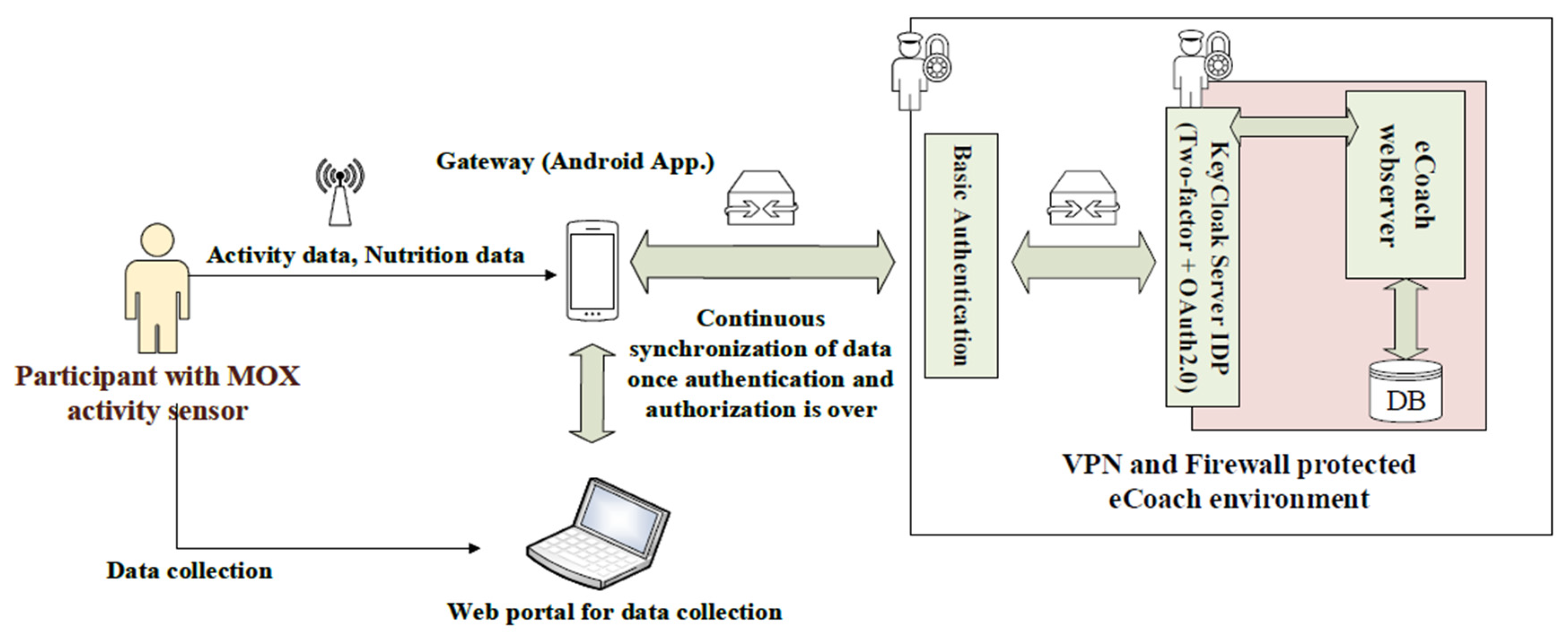
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

Keycloak with Angular and Spring error: GET http://localhost:8180/auth/realms/Storage/protocol/openid-connect/3p-cookies/step1.html 404 (Not Found) - Stack Overflow
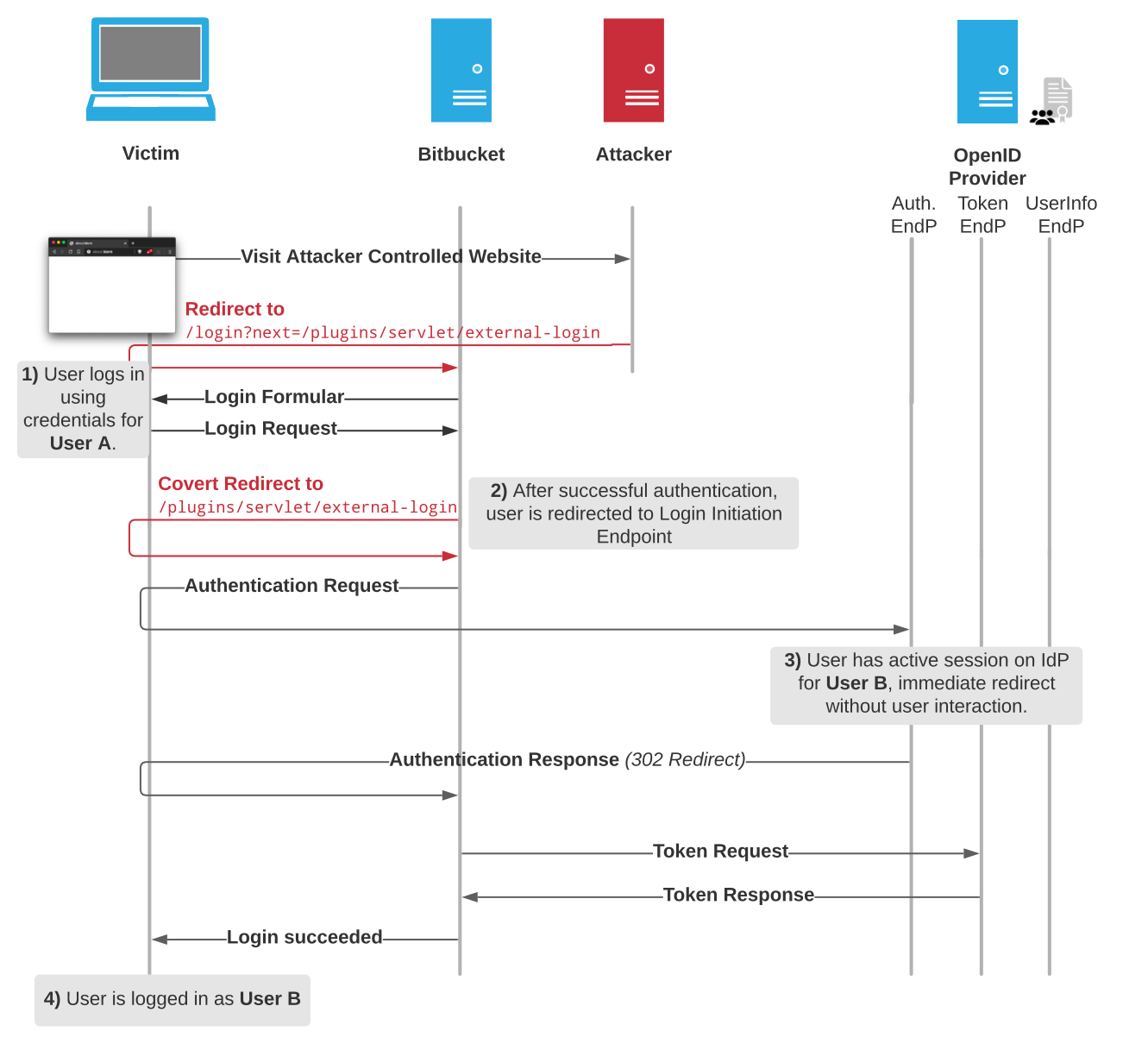
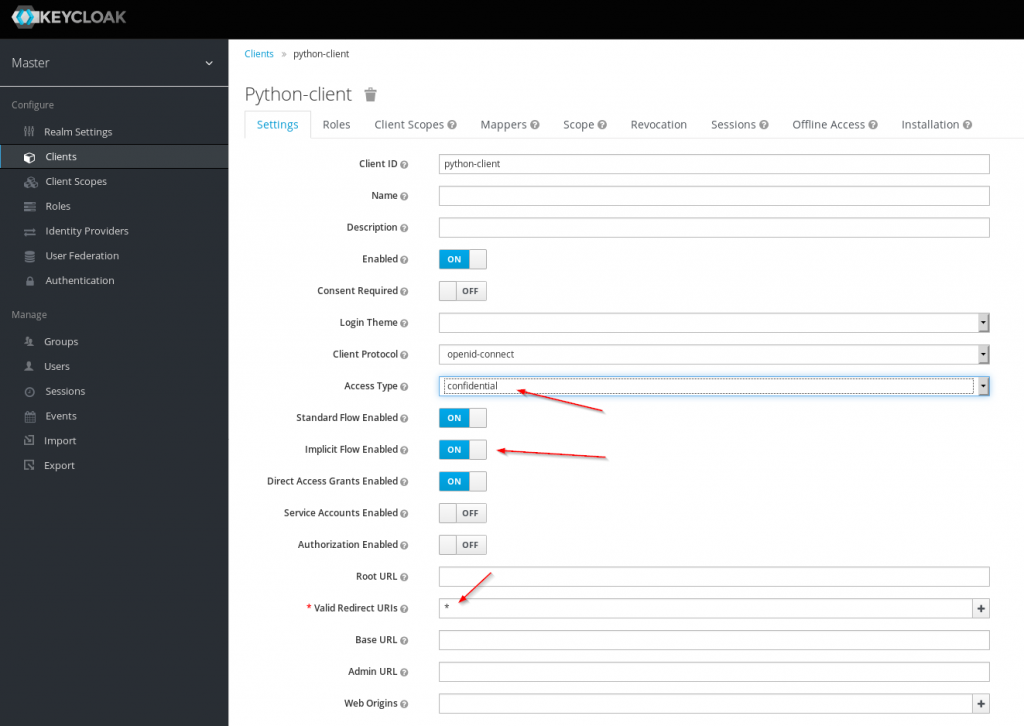
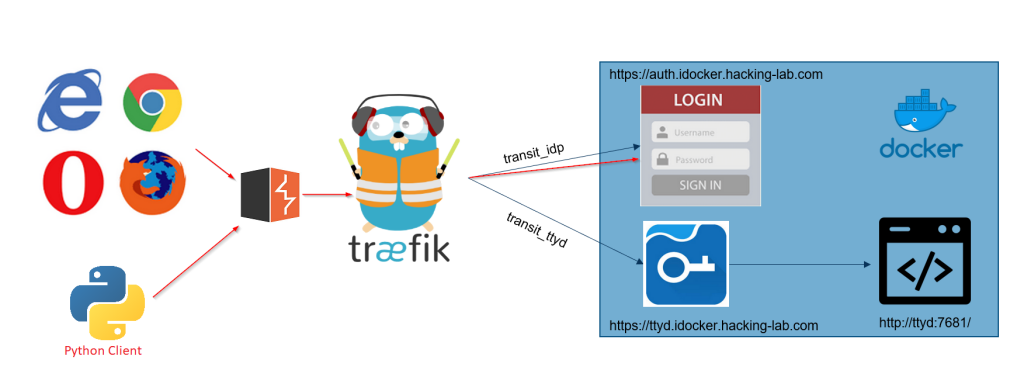
On Web-Security and -Insecurity: Single Sign-On Security: Security Analysis of real-life OpenID Connect Implementations
Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study
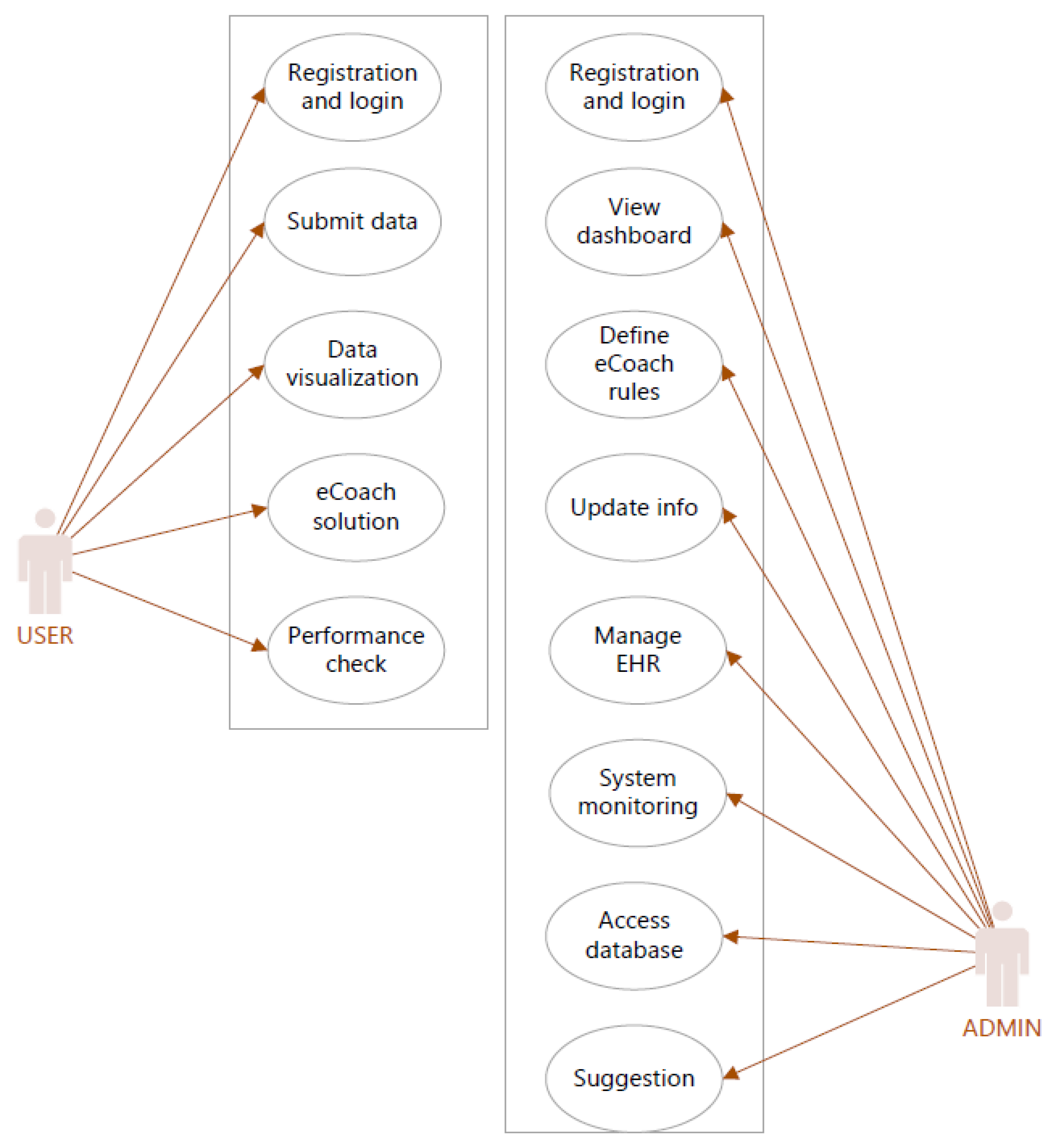
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

On Web-Security and -Insecurity: Single Sign-On Security: Security Analysis of real-life OpenID Connect Implementations
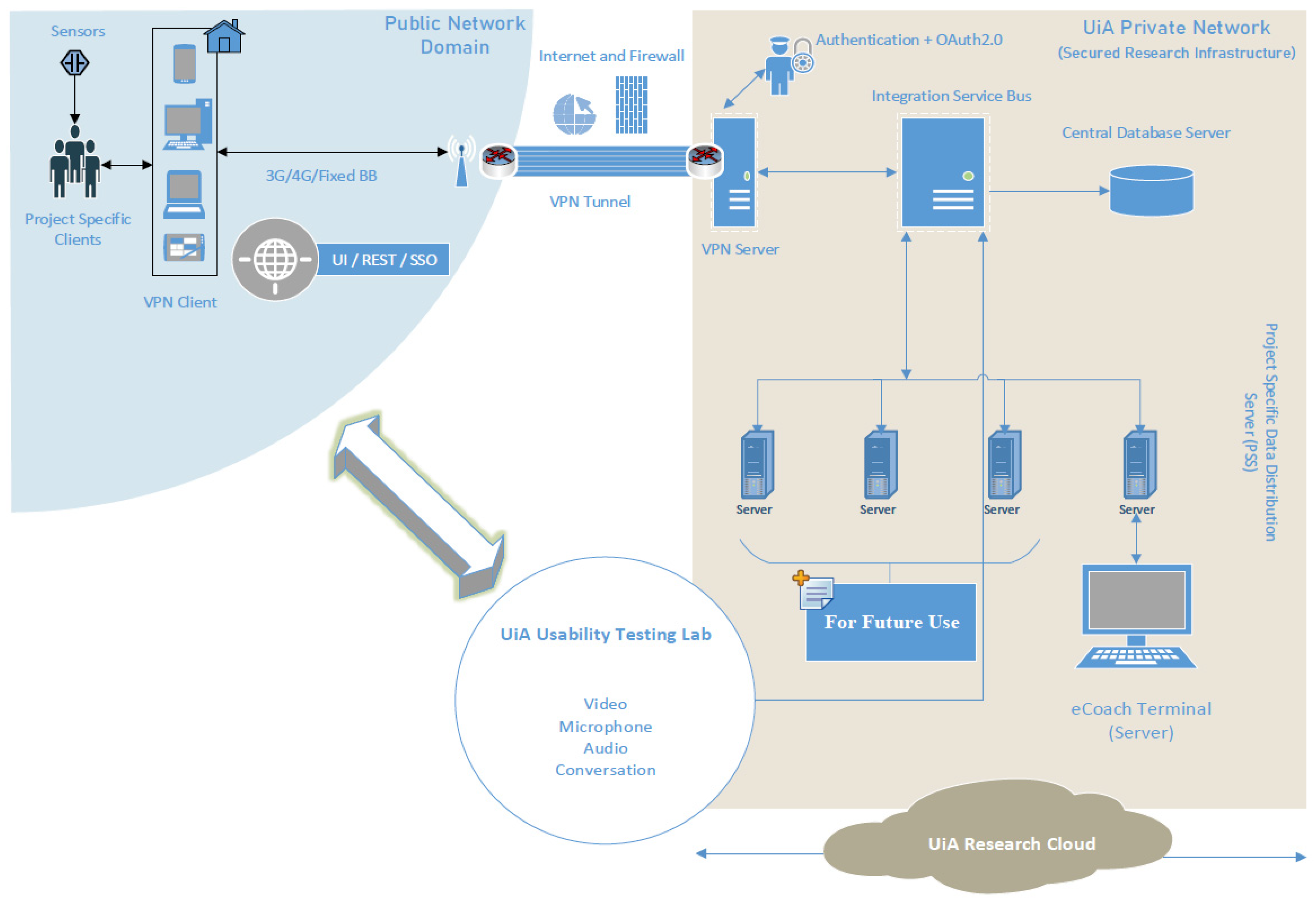
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study
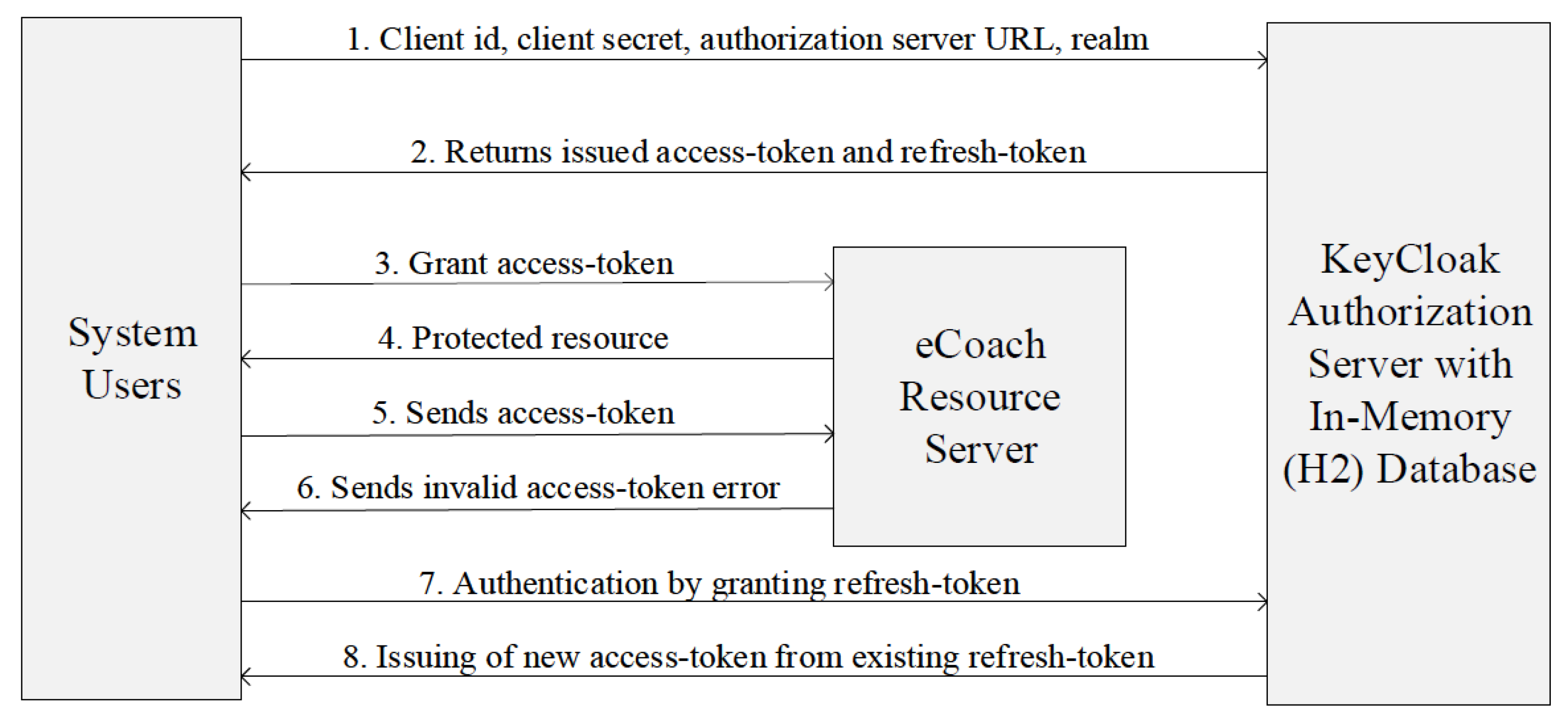
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

On Web-Security and -Insecurity: Single Sign-On Security: Security Analysis of real-life OpenID Connect Implementations
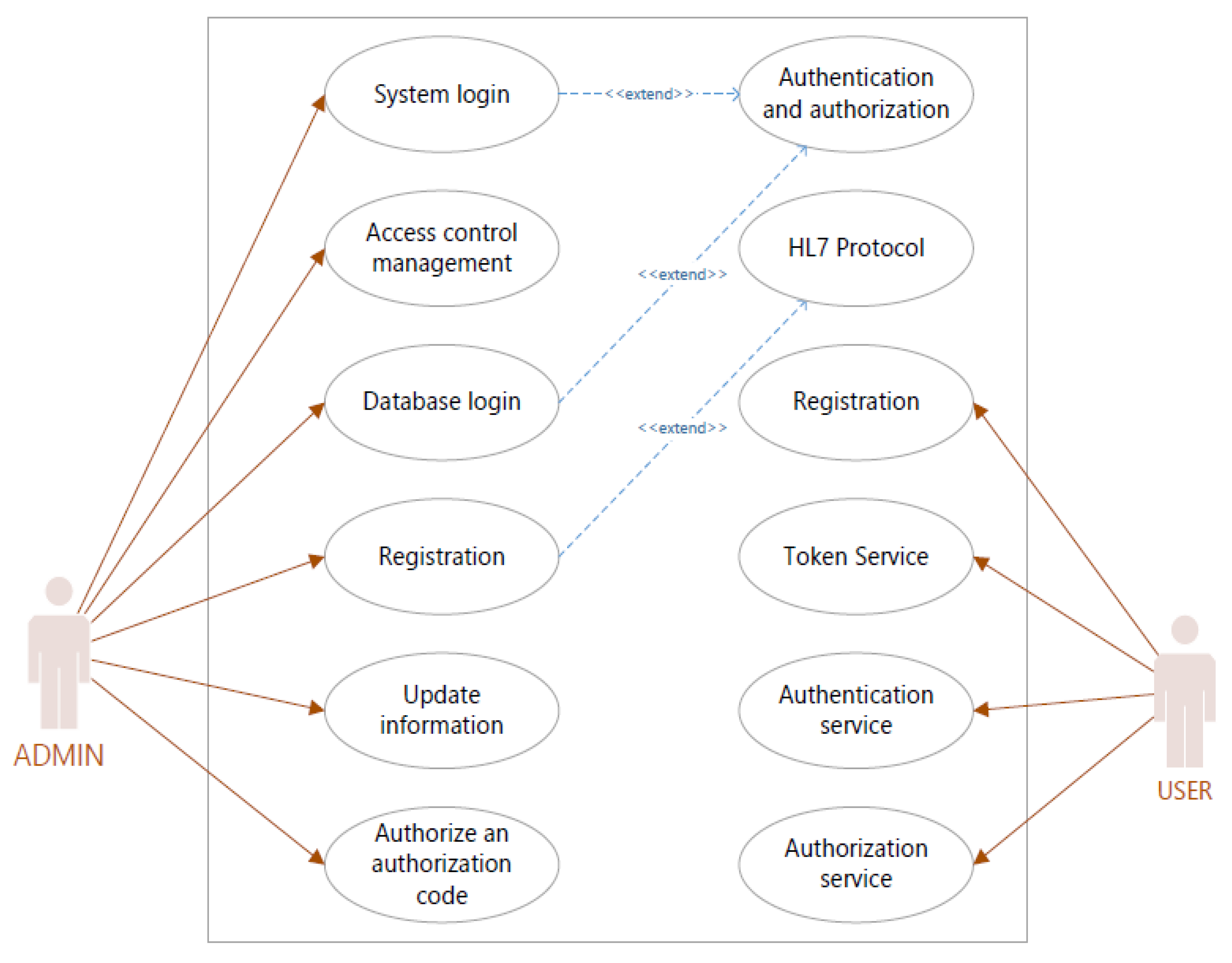
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

PDF) Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

PDF) Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

PDF) Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study